This post will guide you through the steps to create High Availability on FTD. I am using 2 x FTD 2110 Firewalls and Firepower Management Center (FMC).
Before starting the configuration for HA on FMC, we need to make sure that the pre-requisites are met to create HA. Below are the Hardware and Software requirement to create HA in FTD.
Hardware Requirements:
- Both FTD should be the same FTD Model.
- Both FTD should have the same number and types on interfaces.
Software Requirements:
- Both FTD should be part of the same Group or Domain in the FMC.
- Both FTD should have the same firmware version.
- Both FTD should be in the same firewall mode (either routed mode or transparent mode)
- Should have the same NTP configuration.
- There shouldn’t be any uncommitted changes (Verify through clicking on “Deploy” on Top Right hand corner of the FMC.)
- Shouldn’t be configured with DHCP or PPOE in any of their interfaces.
HA Cabling:
Both FTDs should be connected together through dedicated cables for HA using the same interfaces in both devices. The FTD requires “Failover Link” and “State Link”.
These links can be either,
- Dedicated physical links for both Fail-over and State Link.
- Shared physical Interfaces for both Failover and state Link.
- Portchannel link for redundancy.
Note 1: If you are to use Portchannel for HA Links, make sure that you create Portchannel as below.
- No name for the Etherchannel
- Shouldn’t have any Security Zone configured.
- Same Portchannel number at both FTDs.

Note 2: Do not share the data interface with HA link. FTD doesn’t support sharing the data interface with fail-over link.
Note 3: If Portchannel is used for fail-over link, only one interface will be used for Sync and Status check to prevent out-of-order packets. If the 1st link is failed, the next interface in the Portchannel will be used.
If the above is not done, you can’t select Portchannel link as an option when configuring the HA link.
Reference: a details explanation on HA link connectivity can be found in this Cisco Article.
Create a device group:
FTDs can be group together for administrative purpose. This is optional step and not required for the HA configuration.
- Go to Device Management. click on Add -> Add Group.
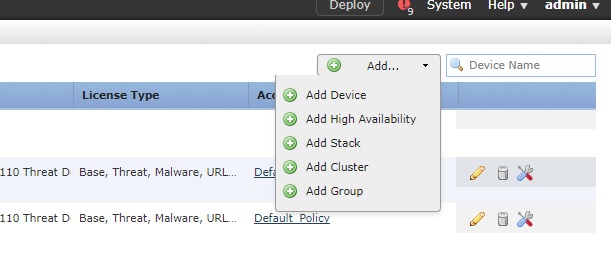
- A new window opens up and will list all the FTDs which are registered in the FMC.

- Give a Name for the group and select the FTDs which you want to be part of the group.

- No you can see that a new device group is created with both FTDs as members.
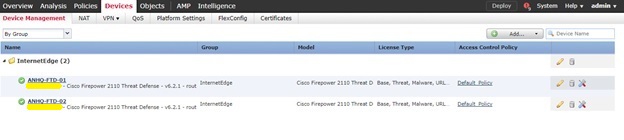
HA Configuration
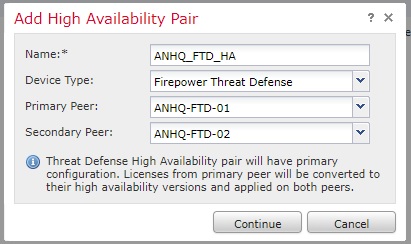
Lets look at the HA configuration. From the Device Mangement, click on Add -> Add High Availability.

- Give a name for the HA Pair and select the FTD devices which will be functioning as Primary Peer and Secondary Peer in the HA group.
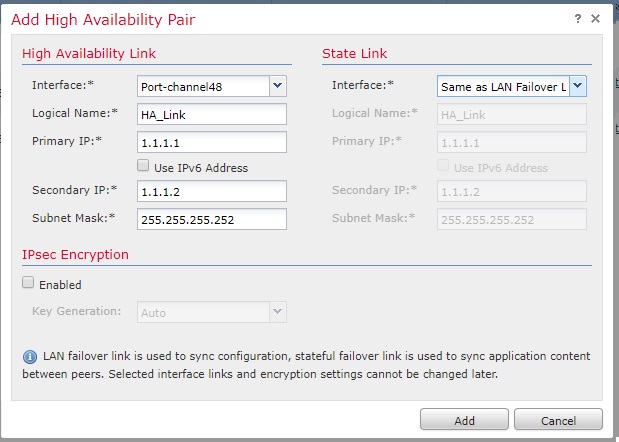
- On the next window, Select the interface which will be used for HA Link. For state link, either you can use a dedicated interface or you can use the HA link. Note that, if you give a name for the Portchannel while you create it, the portchannel interface will not be shown in the drop down list for Interface. Popoulate the details and click Add.
- A reminder on Interface Monitoring and Health policies will be shown. These can be configured later. Make sure you configure the LAN and WAN interfaces for HA monitoring for effective failure detection and HA fail-over.
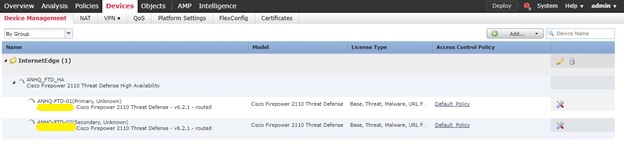
- Wait for few minutes for the HA configuration to be deployed.
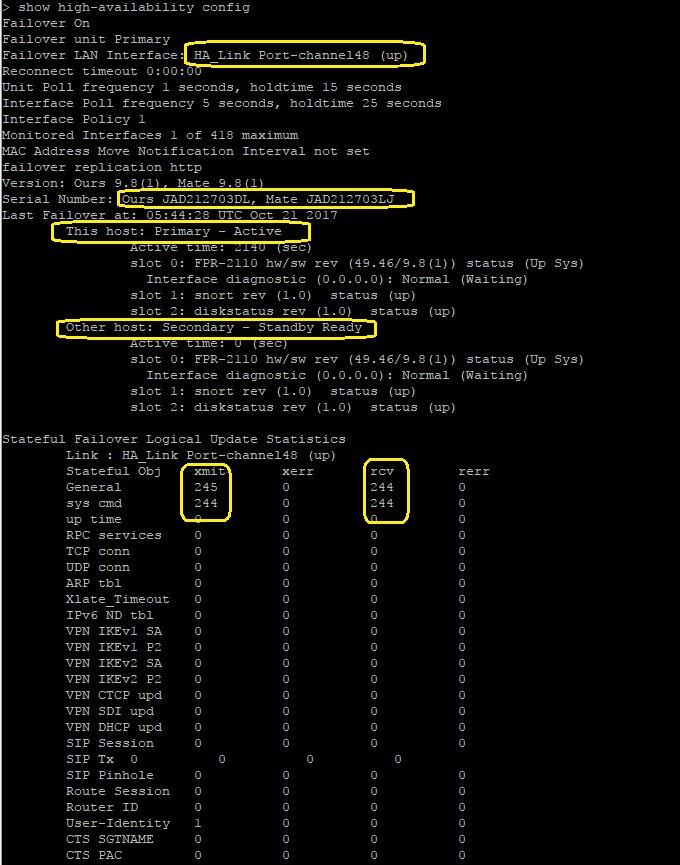
- The status of the HA can also be verified from the CLI. SSH to the FTD (Not FMC) and issue ‘show high-availability config’ command.
Once the HA configuration is deployed successfully, the 2 x FTDs will function as Active-Passive pair. Any further configuration can be deployed to the HA group only – not to the individual FTDs.
